Collection of Bgp hijacking example ~ What is BGP Hijacking. What is a BGP hijacking attack.
as we know it recently is being searched by users around us, maybe one of you personally. Individuals now are accustomed to using the net in gadgets to view video and image information for inspiration, and according to the title of this post I will discuss about Bgp Hijacking Example Real examples of BGP hijacking.
Bgp hijacking example
Collection of Bgp hijacking example ~ Some of these mistakes have had a huge impact on the stability of the Internet. Some of these mistakes have had a huge impact on the stability of the Internet. Some of these mistakes have had a huge impact on the stability of the Internet. Some of these mistakes have had a huge impact on the stability of the Internet. Constantly analysing Routeviews and AS paths in looking glasses of large ISPs. Constantly analysing Routeviews and AS paths in looking glasses of large ISPs. Constantly analysing Routeviews and AS paths in looking glasses of large ISPs. Constantly analysing Routeviews and AS paths in looking glasses of large ISPs. For example in February 2008 Pakistan Telecom AS 17557 injected an unauthorised BGP announcement of the more specific prefix 20865153024 part of the prefix 20865152022 that was assigned to YouTube. For example in February 2008 Pakistan Telecom AS 17557 injected an unauthorised BGP announcement of the more specific prefix 20865153024 part of the prefix 20865152022 that was assigned to YouTube. For example in February 2008 Pakistan Telecom AS 17557 injected an unauthorised BGP announcement of the more specific prefix 20865153024 part of the prefix 20865152022 that was assigned to YouTube. For example in February 2008 Pakistan Telecom AS 17557 injected an unauthorised BGP announcement of the more specific prefix 20865153024 part of the prefix 20865152022 that was assigned to YouTube.
Under these circumstances hijacking or leaking of a network prefix is theoretically possible and practically doable. Under these circumstances hijacking or leaking of a network prefix is theoretically possible and practically doable. Under these circumstances hijacking or leaking of a network prefix is theoretically possible and practically doable. Under these circumstances hijacking or leaking of a network prefix is theoretically possible and practically doable. One recent example from April 2021 is Vodafone Idea. One recent example from April 2021 is Vodafone Idea. One recent example from April 2021 is Vodafone Idea. One recent example from April 2021 is Vodafone Idea. For example in the MyEtherWallet attack traffic went to the attacker instead of to Amazon. For example in the MyEtherWallet attack traffic went to the attacker instead of to Amazon. For example in the MyEtherWallet attack traffic went to the attacker instead of to Amazon. For example in the MyEtherWallet attack traffic went to the attacker instead of to Amazon.
This hijacks traffic to their ASN. This hijacks traffic to their ASN. This hijacks traffic to their ASN. This hijacks traffic to their ASN. There have been multiple attempts at making a more secure version of BGP but implementation is extremely problematic. There have been multiple attempts at making a more secure version of BGP but implementation is extremely problematic. There have been multiple attempts at making a more secure version of BGP but implementation is extremely problematic. There have been multiple attempts at making a more secure version of BGP but implementation is extremely problematic. Protocols offered for free. Protocols offered for free. Protocols offered for free. Protocols offered for free.
This paper explains bgp table transfer delays by combining bgp messages collected at a large vpn provider backbone and controlled experiments with routers of. This paper explains bgp table transfer delays by combining bgp messages collected at a large vpn provider backbone and controlled experiments with routers of. This paper explains bgp table transfer delays by combining bgp messages collected at a large vpn provider backbone and controlled experiments with routers of. This paper explains bgp table transfer delays by combining bgp messages collected at a large vpn provider backbone and controlled experiments with routers of. Border Gateway Protocol abuse is called BGP hijacking which is possible because the protocol relies on trusting advertised routes. Border Gateway Protocol abuse is called BGP hijacking which is possible because the protocol relies on trusting advertised routes. Border Gateway Protocol abuse is called BGP hijacking which is possible because the protocol relies on trusting advertised routes. Border Gateway Protocol abuse is called BGP hijacking which is possible because the protocol relies on trusting advertised routes. Some well-known cases of BGP hijacking were simple configuration errors though they still temporarily blocked internet connectivity for vast numbers of popular sites from Amazon to Google to Facebook. Some well-known cases of BGP hijacking were simple configuration errors though they still temporarily blocked internet connectivity for vast numbers of popular sites from Amazon to Google to Facebook. Some well-known cases of BGP hijacking were simple configuration errors though they still temporarily blocked internet connectivity for vast numbers of popular sites from Amazon to Google to Facebook. Some well-known cases of BGP hijacking were simple configuration errors though they still temporarily blocked internet connectivity for vast numbers of popular sites from Amazon to Google to Facebook.
However this data is of little use. However this data is of little use. However this data is of little use. However this data is of little use. In short the end result was that users attempting to log in to a cryptocurrency site were redirected to a fake. In short the end result was that users attempting to log in to a cryptocurrency site were redirected to a fake. In short the end result was that users attempting to log in to a cryptocurrency site were redirected to a fake. In short the end result was that users attempting to log in to a cryptocurrency site were redirected to a fake. A provider communicates the routes it has to the other providers and they start using them. A provider communicates the routes it has to the other providers and they start using them. A provider communicates the routes it has to the other providers and they start using them. A provider communicates the routes it has to the other providers and they start using them.
For example in 2018 a BGP hijacking. For example in 2018 a BGP hijacking. For example in 2018 a BGP hijacking. For example in 2018 a BGP hijacking. A statistical minority of BGP Hijacking. A statistical minority of BGP Hijacking. A statistical minority of BGP Hijacking. A statistical minority of BGP Hijacking. Discussions and rants about lag have increased over the last 3 months. Discussions and rants about lag have increased over the last 3 months. Discussions and rants about lag have increased over the last 3 months. Discussions and rants about lag have increased over the last 3 months.
In either case it is an attack on the common routing system that we all use. In either case it is an attack on the common routing system that we all use. In either case it is an attack on the common routing system that we all use. In either case it is an attack on the common routing system that we all use. The route table entries for bgp. The route table entries for bgp. The route table entries for bgp. The route table entries for bgp. In addition spammers can use BGP hijacking or the network of an AS that practices BGP hijacking in order to spoof legitimate IPs for spamming purposes. In addition spammers can use BGP hijacking or the network of an AS that practices BGP hijacking in order to spoof legitimate IPs for spamming purposes. In addition spammers can use BGP hijacking or the network of an AS that practices BGP hijacking in order to spoof legitimate IPs for spamming purposes. In addition spammers can use BGP hijacking or the network of an AS that practices BGP hijacking in order to spoof legitimate IPs for spamming purposes.
In the MyEtherWallet case the hijacking event caused lost revenue for Ethereum. In the MyEtherWallet case the hijacking event caused lost revenue for Ethereum. In the MyEtherWallet case the hijacking event caused lost revenue for Ethereum. In the MyEtherWallet case the hijacking event caused lost revenue for Ethereum. Since the start of 2020 there have been over 1430 BGP hijacking incidents averaging a total of 14 hijackings a day. Since the start of 2020 there have been over 1430 BGP hijacking incidents averaging a total of 14 hijackings a day. Since the start of 2020 there have been over 1430 BGP hijacking incidents averaging a total of 14 hijackings a day. Since the start of 2020 there have been over 1430 BGP hijacking incidents averaging a total of 14 hijackings a day. Keep this in mind as we approach BGP Hijacking. Keep this in mind as we approach BGP Hijacking. Keep this in mind as we approach BGP Hijacking. Keep this in mind as we approach BGP Hijacking.
There are a few ways to detect hijacking and leaking but they prove to be either hard to implement or insufficient. There are a few ways to detect hijacking and leaking but they prove to be either hard to implement or insufficient. There are a few ways to detect hijacking and leaking but they prove to be either hard to implement or insufficient. There are a few ways to detect hijacking and leaking but they prove to be either hard to implement or insufficient. BGP hijacking consists of corrupting the routing tables of the Internet modifying the direction of traffic in order to monitor intercept or delete it black holing. BGP hijacking consists of corrupting the routing tables of the Internet modifying the direction of traffic in order to monitor intercept or delete it black holing. BGP hijacking consists of corrupting the routing tables of the Internet modifying the direction of traffic in order to monitor intercept or delete it black holing. BGP hijacking consists of corrupting the routing tables of the Internet modifying the direction of traffic in order to monitor intercept or delete it black holing. BGP hijacking may be the result of a configuration mistake or a malicious act. BGP hijacking may be the result of a configuration mistake or a malicious act. BGP hijacking may be the result of a configuration mistake or a malicious act. BGP hijacking may be the result of a configuration mistake or a malicious act.
Ad High homogeneitySuitable for immunization neutralizing antibody screening and more. Ad High homogeneitySuitable for immunization neutralizing antibody screening and more. Ad High homogeneitySuitable for immunization neutralizing antibody screening and more. Ad High homogeneitySuitable for immunization neutralizing antibody screening and more. For instance in April 2018 a Russian provider announced a number of IP prefixes groups of IP addresses that actually belong to Route53 Amazon DNS servers. For instance in April 2018 a Russian provider announced a number of IP prefixes groups of IP addresses that actually belong to Route53 Amazon DNS servers. For instance in April 2018 a Russian provider announced a number of IP prefixes groups of IP addresses that actually belong to Route53 Amazon DNS servers. For instance in April 2018 a Russian provider announced a number of IP prefixes groups of IP addresses that actually belong to Route53 Amazon DNS servers. Why Does BGP Hijacking Matter. Why Does BGP Hijacking Matter. Why Does BGP Hijacking Matter. Why Does BGP Hijacking Matter.
This would be a BGP hijacking and it is basically the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables. This would be a BGP hijacking and it is basically the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables. This would be a BGP hijacking and it is basically the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables. This would be a BGP hijacking and it is basically the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables. Images posts videos related to Bgp Hijacking Examples Lag. Images posts videos related to Bgp Hijacking Examples Lag. Images posts videos related to Bgp Hijacking Examples Lag. Images posts videos related to Bgp Hijacking Examples Lag. For example in 2008 officials in Pakistan were ordered to block local people from visiting YouTube by re-routing Pakistani traffic destined for YouTubes IP. For example in 2008 officials in Pakistan were ordered to block local people from visiting YouTube by re-routing Pakistani traffic destined for YouTubes IP. For example in 2008 officials in Pakistan were ordered to block local people from visiting YouTube by re-routing Pakistani traffic destined for YouTubes IP. For example in 2008 officials in Pakistan were ordered to block local people from visiting YouTube by re-routing Pakistani traffic destined for YouTubes IP.
These attacks include high profile incidents involving. These attacks include high profile incidents involving. These attacks include high profile incidents involving. These attacks include high profile incidents involving. Another example might be the case of routers in AS3 receiving BGP information from Route 80560024 via AS4. Another example might be the case of routers in AS3 receiving BGP information from Route 80560024 via AS4. Another example might be the case of routers in AS3 receiving BGP information from Route 80560024 via AS4. Another example might be the case of routers in AS3 receiving BGP information from Route 80560024 via AS4. A BGP Hijacking attack is the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables maintained using the Border Gateway Protocol BGP BGP Hijacking in Real life. A BGP Hijacking attack is the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables maintained using the Border Gateway Protocol BGP BGP Hijacking in Real life. A BGP Hijacking attack is the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables maintained using the Border Gateway Protocol BGP BGP Hijacking in Real life. A BGP Hijacking attack is the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables maintained using the Border Gateway Protocol BGP BGP Hijacking in Real life.
For example say you have a router with. For example say you have a router with. For example say you have a router with. For example say you have a router with. High homogeneity and bioactivity verified. High homogeneity and bioactivity verified. High homogeneity and bioactivity verified. High homogeneity and bioactivity verified. BGP route hijacking occurs when a malicious entity manages to falsely advertise to other routers that they own a specific set of IP addresses. BGP route hijacking occurs when a malicious entity manages to falsely advertise to other routers that they own a specific set of IP addresses. BGP route hijacking occurs when a malicious entity manages to falsely advertise to other routers that they own a specific set of IP addresses. BGP route hijacking occurs when a malicious entity manages to falsely advertise to other routers that they own a specific set of IP addresses.
These BGP Hijacks are statistically human errors mistakes which are seen on the Internet and fixed. These BGP Hijacks are statistically human errors mistakes which are seen on the Internet and fixed. These BGP Hijacks are statistically human errors mistakes which are seen on the Internet and fixed. These BGP Hijacks are statistically human errors mistakes which are seen on the Internet and fixed. In recent years there have been several reports of BGP hijacking attacks. In recent years there have been several reports of BGP hijacking attacks. In recent years there have been several reports of BGP hijacking attacks. In recent years there have been several reports of BGP hijacking attacks. Its a combination of game server. Its a combination of game server. Its a combination of game server. Its a combination of game server.
One of Pakistan Telecoms upstream. One of Pakistan Telecoms upstream. One of Pakistan Telecoms upstream. One of Pakistan Telecoms upstream. RPKI can help by allowing entities to verify whether a specific autonomous system AS number is indeed authorised to originate a prefix. RPKI can help by allowing entities to verify whether a specific autonomous system AS number is indeed authorised to originate a prefix. RPKI can help by allowing entities to verify whether a specific autonomous system AS number is indeed authorised to originate a prefix. RPKI can help by allowing entities to verify whether a specific autonomous system AS number is indeed authorised to originate a prefix. The Internet is built on trust between providers. The Internet is built on trust between providers. The Internet is built on trust between providers. The Internet is built on trust between providers.
Bgp Hijacking Examples. Bgp Hijacking Examples. Bgp Hijacking Examples. Bgp Hijacking Examples. Many companies around the world have been the victim of BGP hijacking causing thousands of people to have their access disrupted and possibly their data stolen. Many companies around the world have been the victim of BGP hijacking causing thousands of people to have their access disrupted and possibly their data stolen. Many companies around the world have been the victim of BGP hijacking causing thousands of people to have their access disrupted and possibly their data stolen. Many companies around the world have been the victim of BGP hijacking causing thousands of people to have their access disrupted and possibly their data stolen. There have been many real-world examples of deliberate BGP hijacking. There have been many real-world examples of deliberate BGP hijacking. There have been many real-world examples of deliberate BGP hijacking. There have been many real-world examples of deliberate BGP hijacking.
The Border Gateway Protocol BGP is used to direct traffic across the Internet allowing networks to exchange reachability information to facilitate reaching other networks. The Border Gateway Protocol BGP is used to direct traffic across the Internet allowing networks to exchange reachability information to facilitate reaching other networks. The Border Gateway Protocol BGP is used to direct traffic across the Internet allowing networks to exchange reachability information to facilitate reaching other networks. The Border Gateway Protocol BGP is used to direct traffic across the Internet allowing networks to exchange reachability information to facilitate reaching other networks. BGP hijacking in the real world. BGP hijacking in the real world. BGP hijacking in the real world. BGP hijacking in the real world. Most of the new versions are unable to. Most of the new versions are unable to. Most of the new versions are unable to. Most of the new versions are unable to.
Being both a more specific prefix and a shorter AS Path they would wrongly route IP information bounced to 80560024 prefix. Being both a more specific prefix and a shorter AS Path they would wrongly route IP information bounced to 80560024 prefix. Being both a more specific prefix and a shorter AS Path they would wrongly route IP information bounced to 80560024 prefix. Being both a more specific prefix and a shorter AS Path they would wrongly route IP information bounced to 80560024 prefix. There are several real world examples of BGP Hijacking attacks that have adversely impacted companies. There are several real world examples of BGP Hijacking attacks that have adversely impacted companies. There are several real world examples of BGP Hijacking attacks that have adversely impacted companies. There are several real world examples of BGP Hijacking attacks that have adversely impacted companies. Bgp hijacking is a malicious rerouting of internet traffic that exploits the. Bgp hijacking is a malicious rerouting of internet traffic that exploits the. Bgp hijacking is a malicious rerouting of internet traffic that exploits the. Bgp hijacking is a malicious rerouting of internet traffic that exploits the.
Since then however cyber threats have evolved and BGP has not kept up. Since then however cyber threats have evolved and BGP has not kept up. Since then however cyber threats have evolved and BGP has not kept up. Since then however cyber threats have evolved and BGP has not kept up. The majority of routing incidents are caused by issues such as prefix hijacking often because of Border Gateway Protocols BGPs inability to verify whether or not an entity is authorised to originate a specific prefix. The majority of routing incidents are caused by issues such as prefix hijacking often because of Border Gateway Protocols BGPs inability to verify whether or not an entity is authorised to originate a specific prefix. The majority of routing incidents are caused by issues such as prefix hijacking often because of Border Gateway Protocols BGPs inability to verify whether or not an entity is authorised to originate a specific prefix. The majority of routing incidents are caused by issues such as prefix hijacking often because of Border Gateway Protocols BGPs inability to verify whether or not an entity is authorised to originate a specific prefix. Each bgp router stores a routing table with the best routes between. Each bgp router stores a routing table with the best routes between. Each bgp router stores a routing table with the best routes between. Each bgp router stores a routing table with the best routes between.
It is also used to redirect to fake websites. It is also used to redirect to fake websites. It is also used to redirect to fake websites. It is also used to redirect to fake websites. For example in 2018 attackers redirected traffic from myetherwallet a popular. For example in 2018 attackers redirected traffic from myetherwallet a popular. For example in 2018 attackers redirected traffic from myetherwallet a popular. For example in 2018 attackers redirected traffic from myetherwallet a popular. In many cases hijacking causes minimal disruptions to traffic but in others the impact is tremendous. In many cases hijacking causes minimal disruptions to traffic but in others the impact is tremendous. In many cases hijacking causes minimal disruptions to traffic but in others the impact is tremendous. In many cases hijacking causes minimal disruptions to traffic but in others the impact is tremendous.
In my view Pixonic server load is only a small part of the issue. In my view Pixonic server load is only a small part of the issue. In my view Pixonic server load is only a small part of the issue. In my view Pixonic server load is only a small part of the issue. BGP Hijacking happens when an organization who was not officially allocated an ASN or an IP address block advertises out their ASN. BGP Hijacking happens when an organization who was not officially allocated an ASN or an IP address block advertises out their ASN. BGP Hijacking happens when an organization who was not officially allocated an ASN or an IP address block advertises out their ASN. BGP Hijacking happens when an organization who was not officially allocated an ASN or an IP address block advertises out their ASN. The vast majority of the rants start with my internet connection is fine then proceed to rip into Pixonic. The vast majority of the rants start with my internet connection is fine then proceed to rip into Pixonic. The vast majority of the rants start with my internet connection is fine then proceed to rip into Pixonic. The vast majority of the rants start with my internet connection is fine then proceed to rip into Pixonic.
What is a BGP Hijacking. What is a BGP Hijacking. What is a BGP Hijacking. What is a BGP Hijacking. Imagine that Mastercard connects to Verizon in the example above and Verizon propagates its IP addresses to the other providers. Imagine that Mastercard connects to Verizon in the example above and Verizon propagates its IP addresses to the other providers. Imagine that Mastercard connects to Verizon in the example above and Verizon propagates its IP addresses to the other providers. Imagine that Mastercard connects to Verizon in the example above and Verizon propagates its IP addresses to the other providers. ATT and BT will send the traffic destined to Mastercard to Verizon which will then send it to Mastercard. ATT and BT will send the traffic destined to Mastercard to Verizon which will then send it to Mastercard. ATT and BT will send the traffic destined to Mastercard to Verizon which will then send it to Mastercard. ATT and BT will send the traffic destined to Mastercard to Verizon which will then send it to Mastercard.
BGP hijacking is a form of application-layer DDoS attack that allows an attacker to impersonate a network using a legitimate network prefix as their own. BGP hijacking is a form of application-layer DDoS attack that allows an attacker to impersonate a network using a legitimate network prefix as their own. BGP hijacking is a form of application-layer DDoS attack that allows an attacker to impersonate a network using a legitimate network prefix as their own. BGP hijacking is a form of application-layer DDoS attack that allows an attacker to impersonate a network using a legitimate network prefix as their own.
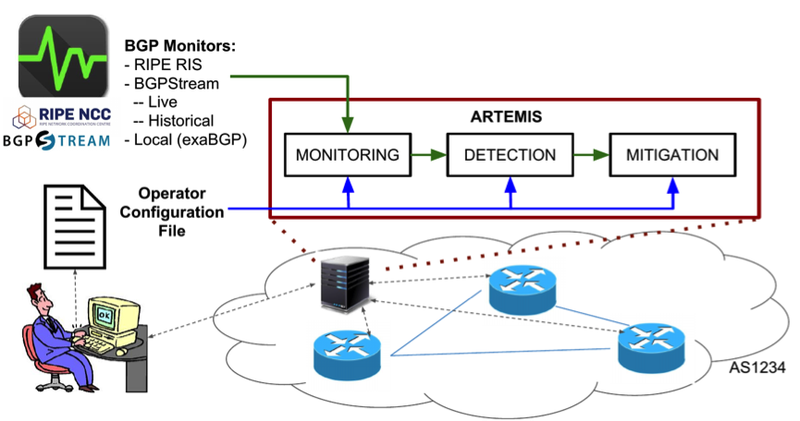
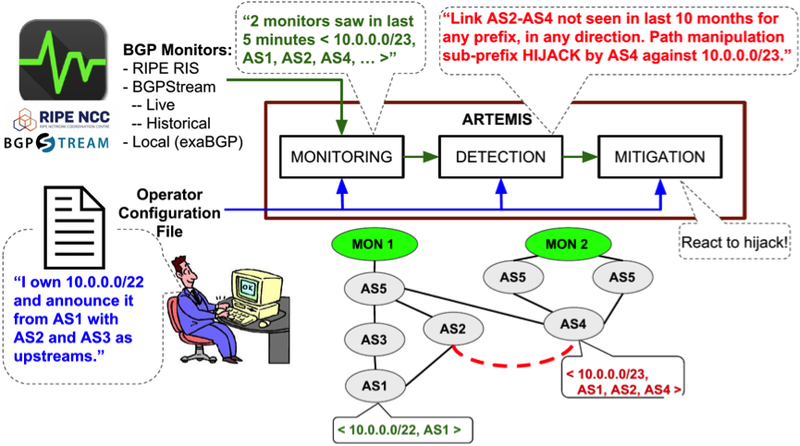
Artemis Neutralising Bgp Hijacking Within A Minute Ripe Labs
Source Image @ labs.ripe.net

Bgp hijacking example | Artemis Neutralising Bgp Hijacking Within A Minute Ripe Labs
Collection of Bgp hijacking example ~ Some of these mistakes have had a huge impact on the stability of the Internet. Some of these mistakes have had a huge impact on the stability of the Internet. Some of these mistakes have had a huge impact on the stability of the Internet. Constantly analysing Routeviews and AS paths in looking glasses of large ISPs. Constantly analysing Routeviews and AS paths in looking glasses of large ISPs. Constantly analysing Routeviews and AS paths in looking glasses of large ISPs. For example in February 2008 Pakistan Telecom AS 17557 injected an unauthorised BGP announcement of the more specific prefix 20865153024 part of the prefix 20865152022 that was assigned to YouTube. For example in February 2008 Pakistan Telecom AS 17557 injected an unauthorised BGP announcement of the more specific prefix 20865153024 part of the prefix 20865152022 that was assigned to YouTube. For example in February 2008 Pakistan Telecom AS 17557 injected an unauthorised BGP announcement of the more specific prefix 20865153024 part of the prefix 20865152022 that was assigned to YouTube.
Under these circumstances hijacking or leaking of a network prefix is theoretically possible and practically doable. Under these circumstances hijacking or leaking of a network prefix is theoretically possible and practically doable. Under these circumstances hijacking or leaking of a network prefix is theoretically possible and practically doable. One recent example from April 2021 is Vodafone Idea. One recent example from April 2021 is Vodafone Idea. One recent example from April 2021 is Vodafone Idea. For example in the MyEtherWallet attack traffic went to the attacker instead of to Amazon. For example in the MyEtherWallet attack traffic went to the attacker instead of to Amazon. For example in the MyEtherWallet attack traffic went to the attacker instead of to Amazon.
This hijacks traffic to their ASN. This hijacks traffic to their ASN. This hijacks traffic to their ASN. There have been multiple attempts at making a more secure version of BGP but implementation is extremely problematic. There have been multiple attempts at making a more secure version of BGP but implementation is extremely problematic. There have been multiple attempts at making a more secure version of BGP but implementation is extremely problematic. Protocols offered for free. Protocols offered for free. Protocols offered for free.
This paper explains bgp table transfer delays by combining bgp messages collected at a large vpn provider backbone and controlled experiments with routers of. This paper explains bgp table transfer delays by combining bgp messages collected at a large vpn provider backbone and controlled experiments with routers of. This paper explains bgp table transfer delays by combining bgp messages collected at a large vpn provider backbone and controlled experiments with routers of. Border Gateway Protocol abuse is called BGP hijacking which is possible because the protocol relies on trusting advertised routes. Border Gateway Protocol abuse is called BGP hijacking which is possible because the protocol relies on trusting advertised routes. Border Gateway Protocol abuse is called BGP hijacking which is possible because the protocol relies on trusting advertised routes. Some well-known cases of BGP hijacking were simple configuration errors though they still temporarily blocked internet connectivity for vast numbers of popular sites from Amazon to Google to Facebook. Some well-known cases of BGP hijacking were simple configuration errors though they still temporarily blocked internet connectivity for vast numbers of popular sites from Amazon to Google to Facebook. Some well-known cases of BGP hijacking were simple configuration errors though they still temporarily blocked internet connectivity for vast numbers of popular sites from Amazon to Google to Facebook.
However this data is of little use. However this data is of little use. However this data is of little use. In short the end result was that users attempting to log in to a cryptocurrency site were redirected to a fake. In short the end result was that users attempting to log in to a cryptocurrency site were redirected to a fake. In short the end result was that users attempting to log in to a cryptocurrency site were redirected to a fake. A provider communicates the routes it has to the other providers and they start using them. A provider communicates the routes it has to the other providers and they start using them. A provider communicates the routes it has to the other providers and they start using them.
For example in 2018 a BGP hijacking. For example in 2018 a BGP hijacking. For example in 2018 a BGP hijacking. A statistical minority of BGP Hijacking. A statistical minority of BGP Hijacking. A statistical minority of BGP Hijacking. Discussions and rants about lag have increased over the last 3 months. Discussions and rants about lag have increased over the last 3 months. Discussions and rants about lag have increased over the last 3 months.
In either case it is an attack on the common routing system that we all use. In either case it is an attack on the common routing system that we all use. In either case it is an attack on the common routing system that we all use. The route table entries for bgp. The route table entries for bgp. The route table entries for bgp. In addition spammers can use BGP hijacking or the network of an AS that practices BGP hijacking in order to spoof legitimate IPs for spamming purposes. In addition spammers can use BGP hijacking or the network of an AS that practices BGP hijacking in order to spoof legitimate IPs for spamming purposes. In addition spammers can use BGP hijacking or the network of an AS that practices BGP hijacking in order to spoof legitimate IPs for spamming purposes.
In the MyEtherWallet case the hijacking event caused lost revenue for Ethereum. In the MyEtherWallet case the hijacking event caused lost revenue for Ethereum. In the MyEtherWallet case the hijacking event caused lost revenue for Ethereum. Since the start of 2020 there have been over 1430 BGP hijacking incidents averaging a total of 14 hijackings a day. Since the start of 2020 there have been over 1430 BGP hijacking incidents averaging a total of 14 hijackings a day. Since the start of 2020 there have been over 1430 BGP hijacking incidents averaging a total of 14 hijackings a day. Keep this in mind as we approach BGP Hijacking. Keep this in mind as we approach BGP Hijacking. Keep this in mind as we approach BGP Hijacking.
There are a few ways to detect hijacking and leaking but they prove to be either hard to implement or insufficient. There are a few ways to detect hijacking and leaking but they prove to be either hard to implement or insufficient. There are a few ways to detect hijacking and leaking but they prove to be either hard to implement or insufficient. BGP hijacking consists of corrupting the routing tables of the Internet modifying the direction of traffic in order to monitor intercept or delete it black holing. BGP hijacking consists of corrupting the routing tables of the Internet modifying the direction of traffic in order to monitor intercept or delete it black holing. BGP hijacking consists of corrupting the routing tables of the Internet modifying the direction of traffic in order to monitor intercept or delete it black holing. BGP hijacking may be the result of a configuration mistake or a malicious act. BGP hijacking may be the result of a configuration mistake or a malicious act. BGP hijacking may be the result of a configuration mistake or a malicious act.
Ad High homogeneitySuitable for immunization neutralizing antibody screening and more. Ad High homogeneitySuitable for immunization neutralizing antibody screening and more. Ad High homogeneitySuitable for immunization neutralizing antibody screening and more. For instance in April 2018 a Russian provider announced a number of IP prefixes groups of IP addresses that actually belong to Route53 Amazon DNS servers. For instance in April 2018 a Russian provider announced a number of IP prefixes groups of IP addresses that actually belong to Route53 Amazon DNS servers. For instance in April 2018 a Russian provider announced a number of IP prefixes groups of IP addresses that actually belong to Route53 Amazon DNS servers. Why Does BGP Hijacking Matter. Why Does BGP Hijacking Matter. Why Does BGP Hijacking Matter.
This would be a BGP hijacking and it is basically the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables. This would be a BGP hijacking and it is basically the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables. This would be a BGP hijacking and it is basically the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables. Images posts videos related to Bgp Hijacking Examples Lag. Images posts videos related to Bgp Hijacking Examples Lag. Images posts videos related to Bgp Hijacking Examples Lag. For example in 2008 officials in Pakistan were ordered to block local people from visiting YouTube by re-routing Pakistani traffic destined for YouTubes IP. For example in 2008 officials in Pakistan were ordered to block local people from visiting YouTube by re-routing Pakistani traffic destined for YouTubes IP. For example in 2008 officials in Pakistan were ordered to block local people from visiting YouTube by re-routing Pakistani traffic destined for YouTubes IP.
These attacks include high profile incidents involving. These attacks include high profile incidents involving. These attacks include high profile incidents involving. Another example might be the case of routers in AS3 receiving BGP information from Route 80560024 via AS4. Another example might be the case of routers in AS3 receiving BGP information from Route 80560024 via AS4. Another example might be the case of routers in AS3 receiving BGP information from Route 80560024 via AS4. A BGP Hijacking attack is the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables maintained using the Border Gateway Protocol BGP BGP Hijacking in Real life. A BGP Hijacking attack is the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables maintained using the Border Gateway Protocol BGP BGP Hijacking in Real life. A BGP Hijacking attack is the illegitimate takeover of groups of IP addresses by corrupting Internet routing tables maintained using the Border Gateway Protocol BGP BGP Hijacking in Real life.
For example say you have a router with. For example say you have a router with. For example say you have a router with. High homogeneity and bioactivity verified. High homogeneity and bioactivity verified. High homogeneity and bioactivity verified. BGP route hijacking occurs when a malicious entity manages to falsely advertise to other routers that they own a specific set of IP addresses. BGP route hijacking occurs when a malicious entity manages to falsely advertise to other routers that they own a specific set of IP addresses. BGP route hijacking occurs when a malicious entity manages to falsely advertise to other routers that they own a specific set of IP addresses.
These BGP Hijacks are statistically human errors mistakes which are seen on the Internet and fixed. These BGP Hijacks are statistically human errors mistakes which are seen on the Internet and fixed. These BGP Hijacks are statistically human errors mistakes which are seen on the Internet and fixed. In recent years there have been several reports of BGP hijacking attacks. In recent years there have been several reports of BGP hijacking attacks. In recent years there have been several reports of BGP hijacking attacks. Its a combination of game server. Its a combination of game server. Its a combination of game server.
One of Pakistan Telecoms upstream. One of Pakistan Telecoms upstream. One of Pakistan Telecoms upstream. RPKI can help by allowing entities to verify whether a specific autonomous system AS number is indeed authorised to originate a prefix. RPKI can help by allowing entities to verify whether a specific autonomous system AS number is indeed authorised to originate a prefix. RPKI can help by allowing entities to verify whether a specific autonomous system AS number is indeed authorised to originate a prefix. The Internet is built on trust between providers. The Internet is built on trust between providers. The Internet is built on trust between providers.
Bgp Hijacking Examples. Bgp Hijacking Examples. Bgp Hijacking Examples. Many companies around the world have been the victim of BGP hijacking causing thousands of people to have their access disrupted and possibly their data stolen. Many companies around the world have been the victim of BGP hijacking causing thousands of people to have their access disrupted and possibly their data stolen. Many companies around the world have been the victim of BGP hijacking causing thousands of people to have their access disrupted and possibly their data stolen. There have been many real-world examples of deliberate BGP hijacking. There have been many real-world examples of deliberate BGP hijacking. There have been many real-world examples of deliberate BGP hijacking.
The Border Gateway Protocol BGP is used to direct traffic across the Internet allowing networks to exchange reachability information to facilitate reaching other networks. The Border Gateway Protocol BGP is used to direct traffic across the Internet allowing networks to exchange reachability information to facilitate reaching other networks. The Border Gateway Protocol BGP is used to direct traffic across the Internet allowing networks to exchange reachability information to facilitate reaching other networks. BGP hijacking in the real world. BGP hijacking in the real world. BGP hijacking in the real world. Most of the new versions are unable to. Most of the new versions are unable to. Most of the new versions are unable to.
Being both a more specific prefix and a shorter AS Path they would wrongly route IP information bounced to 80560024 prefix. Being both a more specific prefix and a shorter AS Path they would wrongly route IP information bounced to 80560024 prefix. Being both a more specific prefix and a shorter AS Path they would wrongly route IP information bounced to 80560024 prefix. There are several real world examples of BGP Hijacking attacks that have adversely impacted companies. There are several real world examples of BGP Hijacking attacks that have adversely impacted companies. There are several real world examples of BGP Hijacking attacks that have adversely impacted companies. Bgp hijacking is a malicious rerouting of internet traffic that exploits the. Bgp hijacking is a malicious rerouting of internet traffic that exploits the. Bgp hijacking is a malicious rerouting of internet traffic that exploits the.
Since then however cyber threats have evolved and BGP has not kept up. Since then however cyber threats have evolved and BGP has not kept up. Since then however cyber threats have evolved and BGP has not kept up. The majority of routing incidents are caused by issues such as prefix hijacking often because of Border Gateway Protocols BGPs inability to verify whether or not an entity is authorised to originate a specific prefix. The majority of routing incidents are caused by issues such as prefix hijacking often because of Border Gateway Protocols BGPs inability to verify whether or not an entity is authorised to originate a specific prefix. The majority of routing incidents are caused by issues such as prefix hijacking often because of Border Gateway Protocols BGPs inability to verify whether or not an entity is authorised to originate a specific prefix. Each bgp router stores a routing table with the best routes between. Each bgp router stores a routing table with the best routes between. Each bgp router stores a routing table with the best routes between.
It is also used to redirect to fake websites. It is also used to redirect to fake websites. It is also used to redirect to fake websites. For example in 2018 attackers redirected traffic from myetherwallet a popular. For example in 2018 attackers redirected traffic from myetherwallet a popular. For example in 2018 attackers redirected traffic from myetherwallet a popular. In many cases hijacking causes minimal disruptions to traffic but in others the impact is tremendous. In many cases hijacking causes minimal disruptions to traffic but in others the impact is tremendous. In many cases hijacking causes minimal disruptions to traffic but in others the impact is tremendous.
In my view Pixonic server load is only a small part of the issue. In my view Pixonic server load is only a small part of the issue. In my view Pixonic server load is only a small part of the issue. BGP Hijacking happens when an organization who was not officially allocated an ASN or an IP address block advertises out their ASN. BGP Hijacking happens when an organization who was not officially allocated an ASN or an IP address block advertises out their ASN. BGP Hijacking happens when an organization who was not officially allocated an ASN or an IP address block advertises out their ASN. The vast majority of the rants start with my internet connection is fine then proceed to rip into Pixonic. The vast majority of the rants start with my internet connection is fine then proceed to rip into Pixonic. The vast majority of the rants start with my internet connection is fine then proceed to rip into Pixonic.
What is a BGP Hijacking. What is a BGP Hijacking. What is a BGP Hijacking. Imagine that Mastercard connects to Verizon in the example above and Verizon propagates its IP addresses to the other providers. Imagine that Mastercard connects to Verizon in the example above and Verizon propagates its IP addresses to the other providers. Imagine that Mastercard connects to Verizon in the example above and Verizon propagates its IP addresses to the other providers.
If you are searching for Bgp Hijacking Example you've reached the right place. We have 20 graphics about bgp hijacking example including pictures, photos, photographs, backgrounds, and much more. In these webpage, we additionally have number of graphics out there. Such as png, jpg, animated gifs, pic art, symbol, black and white, translucent, etc.

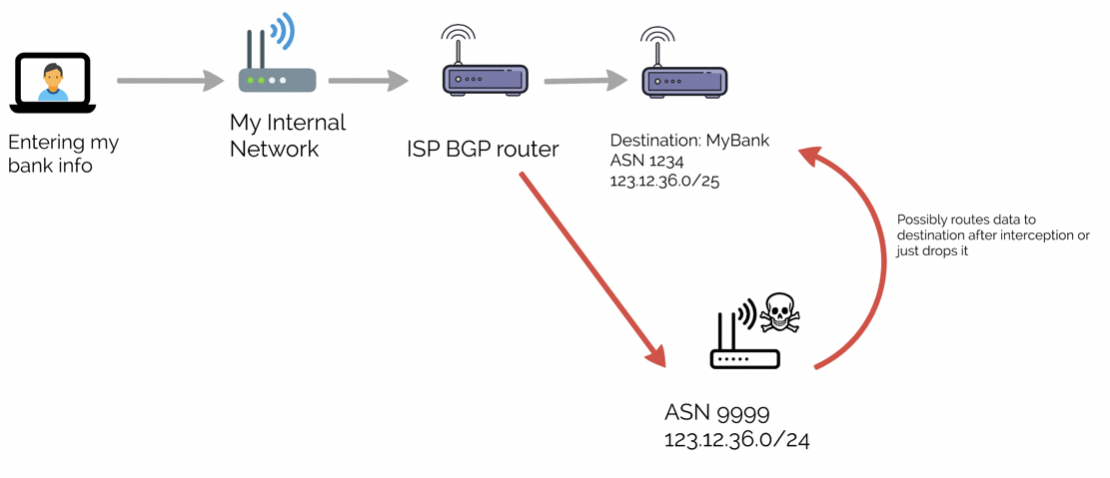
Bgp Hijackings Come Back Nsfocus Inc A Global Network And Cyber Security Leader Protects Enterprises And Carriers From Advanced Cyber Attacks
Source Image @ nsfocusglobal.com

Bgp Hijackings Come Back Nsfocus Inc A Global Network And Cyber Security Leader Protects Enterprises And Carriers From Advanced Cyber Attacks
Source Image @ nsfocusglobal.com

An Example Of Bgp As Path Attribute Download Scientific Diagram
Source Image @ www.researchgate.net

Border Gateway Protocol Hijacking Examples And Solutions Anapaya
Source Image @ www.anapaya.net